In the opening chapter of our journey, we embark on a captivating exploration of our chosen subject, laying the groundwork for a profound understanding. Picture this initial passage as a gateway, inviting you into the heart of our discussion with an enlightening tone. As we step into the intricacies of the topic of Apple ID Recovery Tips, envision preparing for a fascinating odyssey through subsequent discussions.
Embracing an academic writing style, the paragraph employs simple and precise language, weaving a tapestry that unravels the purpose and significance of the impending discourse. This foundational step not only seeks to captivate but also intends to escort you into a realm of comprehension and exploration.
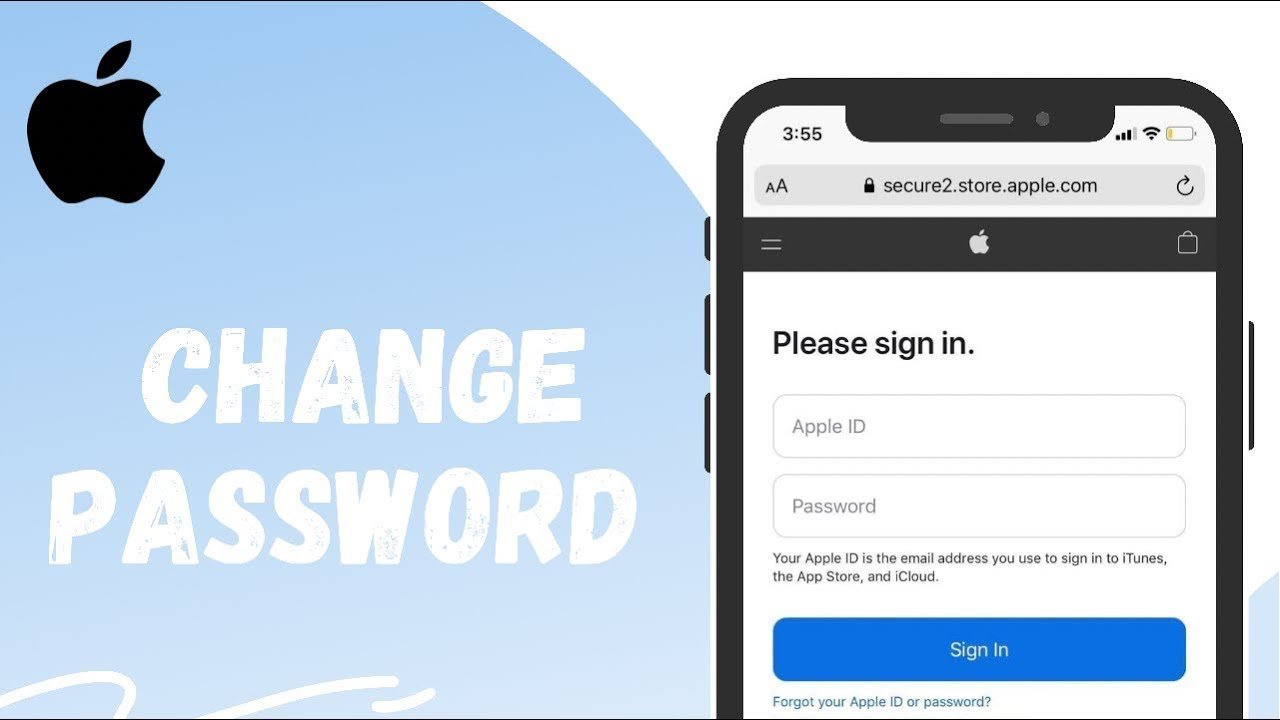
Unlocking the Significance of Apple ID Security
Embarking on exploring Apple ID Recovery Tips is akin to setting sail on a crucial journey to fortify our digital existence. This examination goes beyond the surface, delving deep into the core importance of shielding one’s Apple ID. This scrutiny highlights its vital role in safeguarding our most sensitive personal data amidst the vast digital panorama.
Speaking in an academic tongue, the paragraph takes a holistic approach, painting a vivid picture of the gravity surrounding the protection of this digital key. It unfolds how the security of our Apple ID becomes a linchpin, securing the integrity and confidentiality of personal information—a prelude to a heightened awareness of the imperative need for robust digital protection.
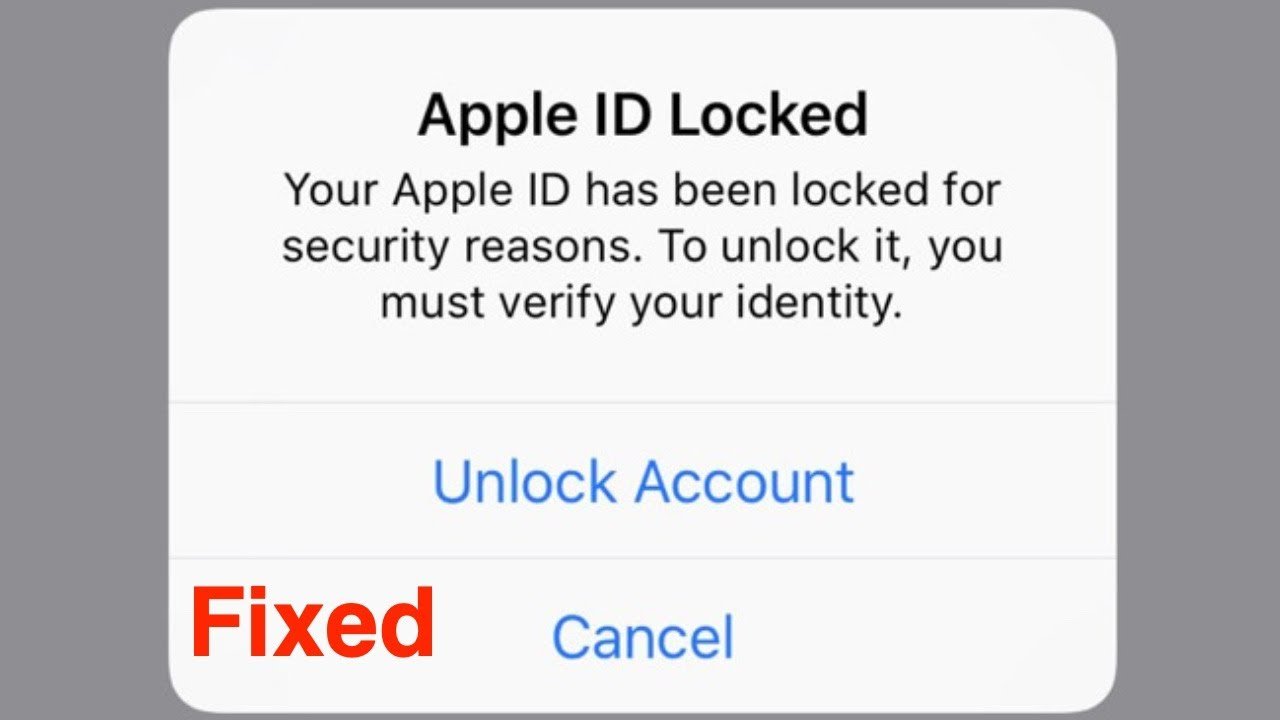
Analyzing the Common Reasons for Forgetting Apple ID Passwords
Exploring the paramount importance of Apple ID security unfolds as a journey into safeguarding our digital existence. This critical examination delves into the core relevance of securing one’s Apple ID, emphasizing its pivotal role in protecting sensitive personal data within the expansive digital landscape.
Adopting an academic tone, the paragraph employs a comprehensive approach to articulate the gravity of safeguarding this digital key. It elucidates how the security of the Apple ID serves as a linchpin, ensuring the integrity and confidentiality of personal information and setting the stage for a heightened awareness of the need for robust digital protection.
Navigating Initial Troubleshooting Steps
Leveraging Apple’s Account Recovery Options
Harnessing Apple’s account recovery options involves skillfully utilizing the tools provided to retrieve vital access credentials. This strategic maneuver employs a nuanced approach to leverage the mechanisms crafted by Apple for account restoration. In an academic tone, the paragraph underscores the importance of comprehending and effectively employing these built-in recovery options.
It emphasizes the user’s active role in recovery, encouraging a thorough exploration of trusted phone numbers and email addresses linked to the Apple ID. Individuals can precisely navigate the restoration journey by utilizing these avenues to ensure a streamlined and successful recovery process.
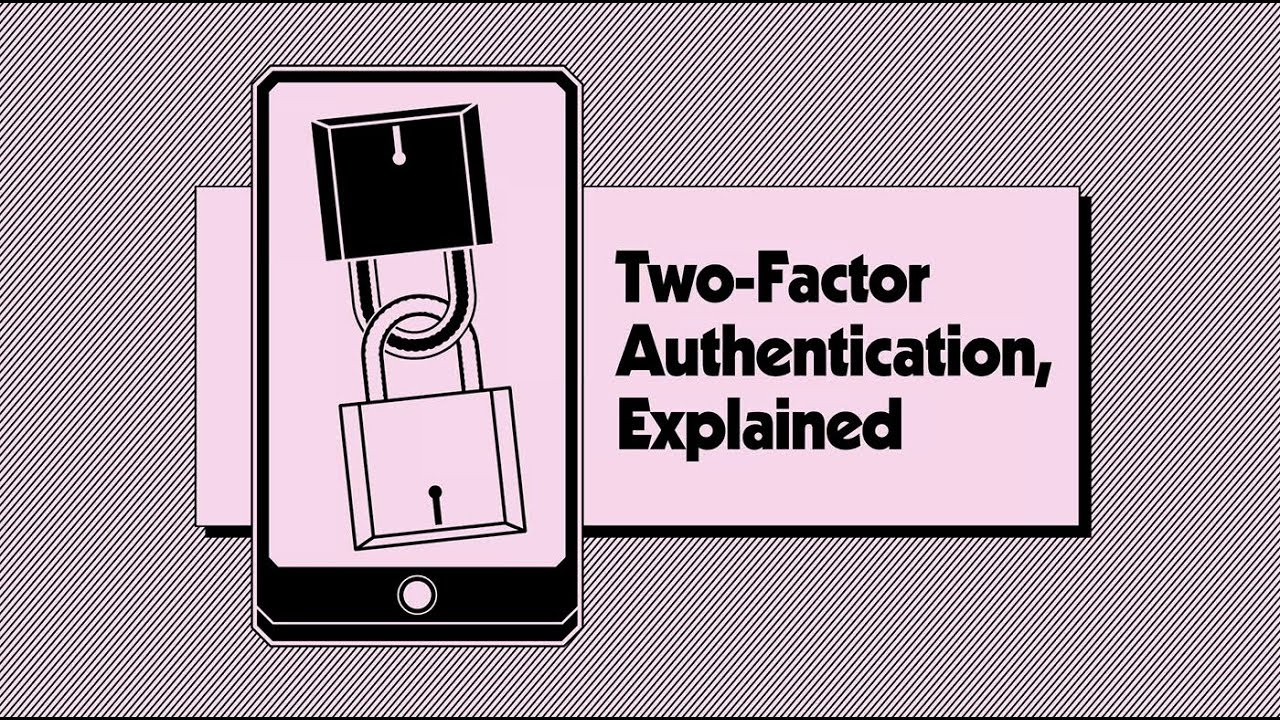
Utilizing Two-Factor Authentication for Verification
Engaging Two-Factor Authentication (2FA) for verification involves deploying an additional layer of security to fortify digital access. This strategic utilization of 2FA is a proactive measure to confirm identity during verification. In an academic tone, the paragraph emphasizes the significance of this supplementary authentication method, elucidating its role in enhancing the security of one’s digital identity.
It advocates for a comprehensive understanding of 2FA’s functionality, underscoring how it is a robust shield against unauthorized access. By incorporating 2FA into the verification process, users contribute to a fortified defense mechanism, elevating the overall security posture.
Employing Security Questions for Account Verification
Deploying security questions for account verification involves strategically utilizing personalized queries to fortify the authentication process. This systematic approach employs user-generated questions to establish a robust layer of identity confirmation.
In an academic tone, the paragraph underscores the importance of these security inquiries, highlighting their integral role in bolstering the security of one’s account. It advocates for thoughtful creation and meticulous maintenance of security questions, emphasizing their effectiveness in thwarting unauthorized access.
By actively incorporating and managing these questions, users contribute to a resilient account verification framework, reinforcing the overall security architecture of their digital identity.
Accessing Apple’s Account Recovery Webpage
Understanding the Account Recovery Waiting Period
Grasping the nuances of the Account Recovery Waiting Period involves comprehending the deliberate interval designed within Apple’s recovery process. This strategic pause, highlighted in an academic tone, is integral to enhancing security measures.
The paragraph accentuates the significance of patience during this waiting period, emphasizing its role in facilitating a thorough recovery. It elucidates how this intentional delay contributes to a meticulous validation process, ensuring the legitimacy of the account recovery attempt.
Users are encouraged to appreciate this waiting period as a vital component in the overall security architecture, reinforcing safeguarding their Apple ID credentials through a measured and thoughtful recovery process.
Recovering Apple ID Password through Trusted Devices
Additionally, recovering the Apple ID password through Trusted Devices involves a strategic approach, utilizing devices recognized and authenticated by the user. As described academically, this method signifies the intentional reliance on specific gadgets for secure password retrieval.
Furthermore, the paragraph underscores the importance of designating devices as trusted, elucidating how this streamlined process contributes to a seamless recovery experience. It encourages users to leverage the familiarity of these devices, showcasing the symbiotic relationship between security and accessibility.
Moreover, individuals confidently navigate the restoration journey by opting for this recovery avenue, utilizing recognized devices as key allies in regaining access to their Apple ID.
Exploring Third-Party Recovery Tools
Delving into Third-Party Recovery Tools involves exploring external Apple ID Recovery Tips retrieval solutions. This analytical approach presented academically, scrutinizes tools beyond Apple’s native options.
The paragraph underlines the need for careful consideration when contemplating these tools, urging users to exercise caution and verify legitimacy. It emphasizes the potential role of third-party tools in the recovery process, underscoring the importance of aligning with reputable and secure options.
By navigating this exploration with discernment, users can broaden their recovery toolkit while ensuring the integrity and privacy of their Apple ID credentials.
Avoiding Scams and Phishing Attempts
Navigating past frauds and phishing efforts requires a vigilant and discriminating position to outsmart deceitful methods. This proactive strategy, unwrapped in an academic demeanor, underscores the pivotal role of discerning genuine recovery methods amidst a sea of deceitful schemes.
Imagine this endeavor as a strategic dance, where your vigilance becomes the choreography, leading you through the intricate steps of online security. In this dance, the emphasis is on recognizing the authentic moves of recovery and sidestepping the deceptive pirouettes of phishing endeavors.
So, in this digital masquerade, your vigilant steps become the shield against the masked attempts to trick and deceive, ensuring your online safety takes center stage.
The paragraph underscores the need for users to stay informed and cautious during the recovery process, steering clear of suspicious requests for sensitive information. It advocates for a proactive mindset, urging individuals to rely solely on official Apple channels and exercise restraint in sharing personal details. By adopting this watchful stance, users contribute to the overall security of their Apple ID, evading potential risks associated with scams and phishing attempts.

Staying Informed about Apple’s Password Policies
Remaining well-informed about Apple’s Password Policies, including ‘How Long Does It Take to Become a Radiology Tech,’ involves a conscientious effort to stay abreast of the company’s evolving guidelines and recommendations. This proactive approach, articulated academically, highlights the significance of aligning one’s recovery efforts with the dynamic landscape of Apple’s security measures.
The paragraph stresses the importance of periodic updates and understanding policy alterations to ensure a synchronized and effective recovery process. Users are encouraged to regard Apple’s password policies as a guiding framework, adapting their practices accordingly.
By maintaining a vigilant awareness of these policies, individuals contribute to a robust and compliant approach to securing and recovering their Apple ID passwords, ensuring a secure and informed navigation of the password recovery landscape.
Contacting Apple Support for Assistance
Contacting Apple Support for assistance involves contacting the dedicated support channels when faced with complexities in Apple ID Recovery Tips.
This purposeful academic engagement underscores the strategic role of seeking personalized assistance. Additionally, the paragraph emphasizes the user’s agency in contacting Apple Support, elucidating how this direct interaction can provide tailored solutions to intricate recovery challenges.
Furthermore, it encourages users to consider this avenue a reliable resource, as it taps into the expertise of Apple’s support professionals for a guided and effective resolution to ensure the successful retrieval of their Apple ID password.

Protecting Your Apple ID After Recovery
Firstly, safeguarding your Apple ID after recovery involves implementing preventive measures to fortify the security of your restored account. Consequently, this strategic approach, articulated academically, underscores the significance of post-recovery actions.
Moreover, the paragraph emphasizes users’ active roles in upholding the integrity of their Apple ID by adopting best practices. Additionally, embarking on the journey of regularly updating passwords, activating extra security features, and remaining watchful against potential threats is akin to fortifying the fortress of your Apple ID.
Finally, picture it weaving a digital shield, where each updated password forms a sturdy link, and activated security features stand as vigilant guardians.
In this digital realm, adherence to these protective rituals isn’t just a routine; it’s a pledge to the longevity of your Apple ID’s security. It’s a commitment to creating a robust defense against lurking risks and a dedication to maintaining a secure digital haven amidst the vast landscapes of the online world. So, let these practices be the keystones of your digital stronghold, standing resilient against the tides of potential threats.
Conclusion
In conclusion, this comprehensive guide navigates the intricate landscape of Apple ID Recovery Tips with a strategic and informed approach. Furthermore, in an academic tone, the paragraph summarizes the key takeaways, emphasizing the importance of understanding the significance of Apple ID security.
Additionally, it highlights the importance of leveraging recovery options and staying abreast of evolving policies. Moreover, it underscores the user’s role in a secure recovery journey.
By adopting the recommended methods, individuals can regain access to their Apple ID and contribute to a heightened digital security awareness. Ultimately, this conclusion is a compass, directing users toward a successful and fortified Apple ID recovery experience. Additionally, following these steps, users can confidently navigate the process and feel reassured about their digital security.
FAQs
Q2: How long does the account recovery process take?
A2: The duration varies, but patience is integral. Apple's account recovery waiting period enhances security and ensures a thorough recovery process.
Q3: Are third-party recovery tools safe to use?
A3: Exercise caution. While some programs may be authentic, it is suggested that you stay with Apple-approved techniques to protect your data.
Q4: What precautions should I take to avoid scams during recovery?
A4: Stay vigilant against phishing attempts. Only use official Apple channels and refrain from sharing sensitive information with unverified sources during recovery.